Threat Watch
Instantly assess your cyber security health with Threat Watch for actionable insights on compromised accounts and dev...
Visit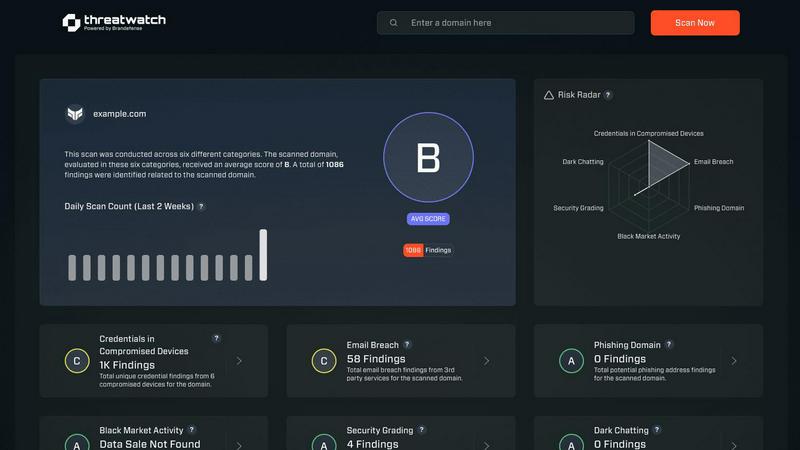
About Threat Watch
Threat Watch is your go-to solution for mastering cybersecurity in the fast-paced digital landscape. This innovative platform analyzes your organization’s assets, vulnerabilities, and exposures to provide a comprehensive overview of your cyber health. Designed for businesses of all sizes, Threat Watch empowers IT professionals and security teams by delivering real-time insights and automated assessments. With its user-friendly interface, you can swiftly identify, prioritize, and mitigate risks before they escalate into serious issues. Whether you are concerned about compromised devices, breached accounts, or phishing attacks, Threat Watch equips you with the intelligence you need to stay ahead of cyber threats. Uncover your cybersecurity health quickly and efficiently, ensuring your organization remains resilient against evolving cyber risks.
Features of Threat Watch
Real-time Cyber Health Insights
Threat Watch offers real-time analysis of your organization's cybersecurity posture, allowing you to monitor vulnerabilities and exposures instantaneously. This feature ensures timely decision-making and helps mitigate risks before they can be exploited.
Comprehensive Asset Evaluation
This feature evaluates critical security categories, providing a detailed assessment of your organization’s assets. By understanding where your vulnerabilities lie, you can allocate resources effectively and enhance your overall security strategy.
Automated Risk Assessments
With automated assessments, Threat Watch streamlines the process of identifying potential risks. This efficiency allows security teams to focus on high-priority threats, improving response times and reducing the likelihood of breaches.
Dark Web Monitoring
Threat Watch continuously scans the dark web for compromised credentials and sensitive data related to your organization. This proactive approach enables you to take immediate action against potential threats, safeguarding your digital assets.
Use Cases of Threat Watch
Proactive Vulnerability Management
Organizations can leverage Threat Watch to establish a proactive stance on vulnerability management. By continuously scanning for weaknesses, teams can address potential issues before they become critical threats.
Incident Response Optimization
Security teams can use Threat Watch to optimize incident response strategies. With real-time insights, they can prioritize threats effectively and allocate resources where they are needed most, minimizing potential damage.
Compliance Assurance
Businesses can utilize Threat Watch to ensure compliance with industry regulations and standards. By regularly assessing cyber health, organizations can demonstrate adherence to security protocols, reducing liability risks.
Employee Education on Phishing Threats
Threat Watch can be instrumental in training employees about phishing threats. By identifying and monitoring phishing addresses, organizations can educate their workforce on recognizing and avoiding potential scams.
Frequently Asked Questions
How does Threat Watch analyze my organization's assets?
Threat Watch utilizes advanced algorithms to scan your organization's digital footprint. It evaluates assets against known vulnerabilities and exposures, offering a comprehensive picture of cyber health.
Can Threat Watch help with compliance requirements?
Yes, Threat Watch is designed to assist organizations in meeting various compliance requirements. Its regular assessments and reports can provide evidence of security measures in place, helping to fulfill regulatory obligations.
Is Threat Watch suitable for small businesses?
Absolutely! Threat Watch is versatile and scalable, making it suitable for organizations of all sizes. Its user-friendly interface ensures that small businesses can effectively manage their cybersecurity without extensive resources.
What types of threats can Threat Watch identify?
Threat Watch can identify a range of cyber threats, including compromised devices, breached accounts, phishing attempts, and dark web contents. Its comprehensive monitoring ensures that you are informed of potential risks as they arise.
You may also like:
finban
Plan your liquidity so you can make decisions with confidence: hiring, taxes, projects, investments. Get started quickly, without Excel chaos.
Manage Bankroll
Privacy-first finance tracker for traders, poker players, and sports bettors. AI-powered natural language parsing with intentional manual entry.
Zignt
Zignt simplifies contract management with automated templates, instant signing, and bank-level security for seamless ...